This document is straight up for sysadmins and PowerShell junkies (and Microsoft, assuming anyone from stumbles across this). Beginning somewhere around Windows 10, Version 1909 (18363.1256), an error appeared making long standing PowerShell scripts suddenly begin to fail.
The Commmand
Add-VpnConnection -Name ($ikename=Read-Host "VPN Name") -ServerAddress ($fqdnval=Read-Host "fqdn") -TunnelType Ikev2 -EncryptionLevel Maximum -AuthenticationMethod EAP -RememberCredential -SplitTunneling $true -PassThru
The Errors
If this command is run without elevated privileges, it will fail with the following error :
Add-VpnConnection : VPN connection test ikev2 cannot be added to the global user connections. : Access is denied.
At line:1 char:1
+ Add-VpnConnection -Name $ikename -ServerAddress $fqdnval -TunnelType ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (test ikev2:root/Microsoft/...S_VpnConnection) [Add-VpnConnection], CimException
+ FullyQualifiedErrorId : WIN32 5,Add-VpnConnection
It would be easy enough to assume, then, that this should simply be run with elevated privileges. And, indeed, the connection is created successfully. However if you return to a non-elevated PowerShell window and run the following :
Get-VPNConnection -Name $ikename
The connection will be appear to be missing, and generates the following error :
Get-VpnConnection : VPN connection test ikev2 was not found. : The system could not find the phone book entry for this
connection.
At line:1 char:1
+ Get-VpnConnection -Name "test ikev2"
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (asprv ikev2 36:root/Microsoft/...S_VpnConnection) [Get-VpnConnection], CimException
+ FullyQualifiedErrorId : VPN 623,Get-VpnConnection
It just doesn’t appear. To get it to appear, you must use the following :
Get-VPNConnection -Name $ikename -AllUserConnection
Which produces a result similar to the following :
Name : test ikev2
ServerAddress : host.eclat.tech
AllUserConnection : True
Guid : {F3FCC298-89EB-46C5-8D14-BFBD03FC1879}
TunnelType : Ikev2
AuthenticationMethod : {Eap}
EncryptionLevel : Custom
L2tpIPsecAuth :
UseWinlogonCredential : False
EapConfigXmlStream : #document
ConnectionStatus : Disconnected
RememberCredential : True
SplitTunneling : True
DnsSuffix :
IdleDisconnectSeconds : 0
The important part to note here is this line :
AllUserConnection : True
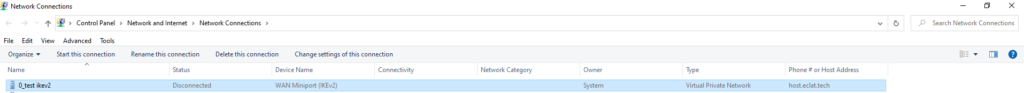
You can also see this in Control Panel\Network and Internet\Network Connections
Note the Owner column lists “System” instead of computername\username or domainname\username.
Digging Deeper
Turns out, now, despite the lack of a flag to set the connection as an All User Connection, when the command above is run, it stores the connection in :
%ProgramData%\Microsoft\Network\connections\Pbk\rasphone.pbk
If you open that document with a text editor, you will see only the entries that have been created as though they had been configured for AllUserConnection $true. But, why?
The bug
Turns out, the bug comes from the following flag :
-SplitTunneling $false
Note that there is nothing inherent to Split Tunneling that should suggest the VPN should automatically be changed from a “Current User” or “Me Only” to an “All Users.” Frankly, this is a security risk, too.
The Workaround
Okay, so, here’s the workaround – separate out the -SplitTunneling from the rest of the command, and add that in a second command. Note that it no longer matters if you add the connection from an elevated PowerShell prompt or not.
Add-VpnConnection -Name ($ikename=Read-Host "VPN Name") -ServerAddress ($fqdnval=Read-Host "fqdn") -TunnelType Ikev2 -EncryptionLevel Maximum -AuthenticationMethod EAP -RememberCredential -PassThru
Get-VPNConnection -Name $ikename | Set-VPNConnection -SplitTunneling $true
Now, you will see the correct owner listed in Network Connections, and the Get-VPNConnection command will display the connection without issue. However, there is still a problem.
More Bugs?
Remember that connection that appears with the owner as “System?” You want that gone, right? This is supposed to be the command to remove it :
Remove-VPNConnection $ikename -Force
But that produces the following error – whether in an elevated PowerShell window or not :
Remove-VpnConnection : VPN connection test ikev2 was not found. : The system could not find the phone book entry for this
connection.
At line:1 char:1
+ Remove-VpnConnection -Name "test ikev2 " -Force
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (test ikev2:root/Microsoft/...S_VpnConnection) [Remove-VpnConnection], CimExceptio
n
+ FullyQualifiedErrorId : VPN 623,Remove-VpnConnection
Not found? That can’t be right. You check rasphone.pbk – and it’s there. It shows up in Network Connections. WT[H,F]?
Remember, this is happening in an elevated PowerShell prompt. Still, you try this :
Remove-VPNConnection $ikename -AllUserConnection -Force
And it finally works. Now, that seems rather buggy, doesn’t it?!!! Fortunately, this one is rather consistent. Even in an elevated prompt, the Get-VpnConnection STILL won’t show all user connections without that -AllUserConnection flag. It’s a little irritating, especially since you can’t see ALL the vpn connections in a single list, but it can be useful if you are trying to find connections that are not supposed to be one way or the other.
Of course, by now you probably just want to rename that final successful entry, right? Yeah, good luck with that. Best just to delete and re-create or rename it through the GUI and move on.
Good luck!