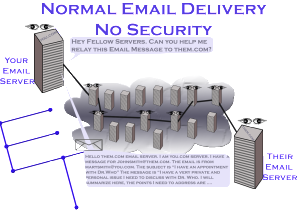
An existing customer asked me to recommend a Network Attached Server (NAS) for use in backing up their primary computer and, rather than keep the recommendations to just them, I thought I’d share a few thoughts. The limitations of this review are that I haven’t physically handled most of them, and this not be a comprehensive review of the options out there as there are altogether too many to choose from, so this will only cover a few select units. Also, there is no way in a review like this to cover all of the features offered in each unit.
Our goal here is to back up a a single computer using Acronis True Image Home, and there must be capacity for multiple copies of backups, going back a month. The system to be backed up is a typical small office computer, with about 250GB of hard drive space used. A NAS is preferred, because it can be placed in a physically different location, reducing the risk of theft during a break in.
Qnap TS-251+ 2-Bay, 6TB(2x 3TB NAS Drive) Intel 2.0GHz Quad-Core CPU (TS-251+-2G-23R-US)
Bottom Line : I DO recommend the QNAP TS-251+2G for very small businesses and people at home
Prices found online : $340 plus your choice of hard drives
| GOOD | BAD |
| 2x Gigabit Ethernet | |
| Hot Swappable drives | |
| Quad Core Processor | Celeron J900 |
| 2GB RAM | |
| Raid 1,0 | |
| SATA III (6Gb/s) | |
| Firewall | |
| Supports Encryption | |
| User based Sharing | |
| Manufacturer Virus Scan/Security Software | No Third Party Security Software |
| Installable SSL Certificates |
QNAP TS-251 2-Bay Personal Cloud NAS, Intel 2.41GHz Dual Core CPU with Media Transcoding (TS-251-US)
Bottom Line : I DO recommend the QNAP TS-251 for very small businesses and users at home.
Prices found online : $250 plus your choice of hard drives
| GOOD | BAD |
| 2x Gigabit Ethernet | |
| Hot Swappable drives | |
| Dual Core Processor | Celeron J1800 |
| 1GB RAM | |
| Raid 1,0 | |
| SATA III (6Gb/s) | |
| Firewall | |
| Supports Encryption | |
| User based Sharing | |
| Manufacturer Virus Scan/Security Software | No Third Party Security Software |
| Installable SSL Certificates |
The choice between the TS-251 and 251+ is really about the processor. If you’re willing to part with the extra $90, you’ll definitely get farther with the 251+ . In either case, I do wish the NAS manufacturers would go ahead and move into the i series processors, even if it does cost a few extra dollars to do so.
Synology DS216j Diskless System NAS DiskStation
Bottom line : I DO recommend this system for very small business and home use. I wouldn’t use it with more than 2 computers at once, but it is a solid device with a lot of positive features.
Prices found online : $170 Plus your choice of hard drives
File format is EXT4.
| GOOD | BAD |
| Gigabit Ethernet | |
| SATA III | |
| 512MB RAM | |
| Dual Core Processor | |
| Supports Encryption | |
| User based sharing | |
| RAID 0,1 | Drives NOT hot swappable |
| Firewall | |
| Manufacturer Virus Scan/Security Software | No third party security software |
| Installable SSL Certificates |
Syno_UsersGuide_NAServer_enu.pdf
WD My Cloud 3 TB
Bottom Line : I do NOT recommend this for business or personal use, except in very specific circumstances.
My customer picked this up (model WDBCTL0030HWT-NESN) , quite inexpensively and, from its spec sheet, it seemed like a good option. Once we started using it, however, its reality fell far short of expectation. As a result, its review is considerably shorter than those I do recommend.
| GOOD | BAD |
| Easy Setup | Poor Security |
| Low Cost | |
| Drives are included and installed | Drives are not hot swappable |
While I only had my hands on this unit briefly, the security problems I ran into were as follows :
- Returning to the setup screen in any web browser allowed immediate ability to edit the configuration of the NAS, without being challenged for a password.
- UNC (\\servername) from a Windows based computer allowed full, unchallenged access to the data stored on the NAS. This makes the data vulnerable to intentional or unintentional deletion by an employee, or worse due to malware, ransomware and infiltrators.
Even at home I have serious reservations about this device, and I wouldn’t recommend it to anyone until the company updates the firmware to ensure basic security is in place first.
If you have more than 2 computers to backup, or are planning to use the NAS as a primary file server, then you should consider a 4 Bay NAS, like the QNAP TS-453A. More on that in another post.






 Introducing Microsoft Edge in Windows 10
Introducing Microsoft Edge in Windows 10