Dan Yedinak is founder and owner of ECLAT Tech. These days Dan finds himself focusing primarily in three areas. Small Business Consulting is his area of professional expertise. Whether it is managing a technology project, like site to site VPNs, router and firewall configuration and management, site wide wireless, servers, or websites and internet marketing, or installing and managing the systems of a small business, you can count on Dan to both get the job done, and work with you to document the work so that YOU have control over your Technology, whenever you need it. Dan also devotes a whole lot of time to Autism and to Gender and Socioeconomic Equity.
Author's posts
Nov 28
We’re falling behind on system security updates and Google and Apple are to blame
Security updates on personal devices are critical. But many people don’t do them. Now, limiting the blame to just two companies is understating the issue, and if all this sounds a little harsh, stick with me, and I’ll explain, beginning with an analogous scenario. We have updated your car You are driving to work, and …
Oct 05
Network Attached Storage for Backups Reviews and Recommendations
An existing customer asked me to recommend a Network Attached Server (NAS) for use in backing up their primary computer and, rather than keep the recommendations to just them, I thought I’d share a few thoughts. The limitations of this review are that I haven’t physically handled most of them, and this not be a …
Sep 06
Text messaging for business correspondence is bad business practice
How do you know when text messaging crosses the line?
Here are a few general guidelines to follow :
If your text message has paragraphs – stop and move to email
If your text message will need to be referred back to at any time – it should be an email
If the message contains sensitive information, especially in a regulated industry (such as healthcare, or finance) – stop texting and use an encrypted communication method.
If your text message is becoming a business conversation – call, or email
If you can’t finish the text message exchange in 4 brief texts back and forth, it’s time to stop
Aug 11
ECLAT.TECH Proud to support Sean’s Run for ARROAutism – 2016
On Saturday, August 20th, ECLAT.TECH will once again be on site for the annual Sean’s Run for ARROAutism. The annual event, largely a 5K/10K walk/run raises money for families in Multnomah, Washington and Clackamas families during the holidays. How Sean’s Run Helps Oregon Families Until this year, most families in Oregon did not have access …
Jun 16
Do NOT punish employees for being victims
Phishing Phishing is when someone tries to convince you to click on a link and enter information on a website that is pretending to be something else, for the purposes of obtaining confidential information about you for an unknown, and probably illegitimate, purpose. Punish the Victims? An article, published on TechTarget, proposes to punish the people …
Jun 01
Farewell to Internet Explorer – Hello Edge
The year is 1995. AOL rules supreme as the internet service provider of choice, and Microsoft has just released a new operating system called Windows 95, a replacement for Windows 3.11. Personal computers were few, and far between, and those few people had were treated like gold. And, for good reason. A top of the …
Oct 29
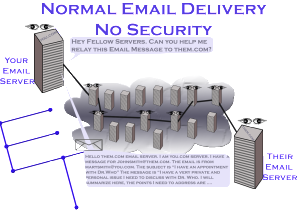
What do you mean my email is not secure?
Email security is a challenging topic to understand. While progress has been made to improve that security, there are many, many variables that make it impossible for you to know if the email you are sending is being delivered securely to its final destination. Yes, I did say impossible. Even a seasoned server administrator could not …